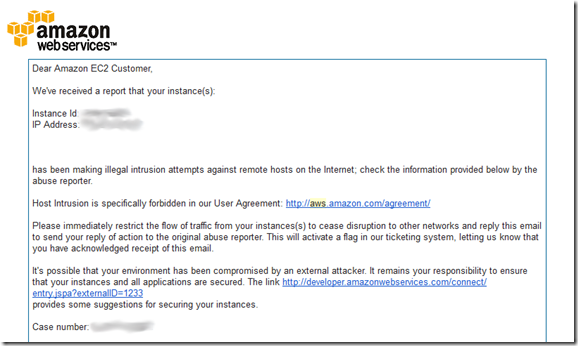
This blog had been extremely quiet for several months while twitter has become my ‘go to’ vehicle for quick rants. Or so I thought, until I received 2 notices from AWS (my blog is hosted on an EC2 instance) saying that my instance had been reported for abusing the terms of service.
The worst part about receiving news like this is the immediate reaction is to drop everything and dive in to investigate, however often other things supervene, and so after quickly cycling through ‘shock and denial’ and ‘pain and guilt’ I decided to turn off the instance to prevent further ‘damage’ arising from its misuse, and to fix it up at a later date.
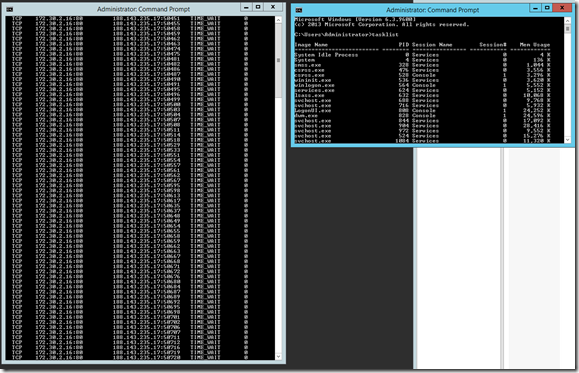
A few days later I turned the instance back on and had a look at what was happening network-wise on the server. Netstat revealed hundreds of instances of process with ID 0 (PID0 is normally reserved for the system idle process) listening on port 80 communicating with a client located somewhere in St. Petersburg. Seems legit.
I’d taken some basic security precautions – preventing all inbound ports except port 80 and RDP from my ‘home’ IP address and running app pools under low-privileged accounts, but clearly it wasn’t enough. I’m not sure how I was owned – my windows updates were fairly sporadic, so even though it was a ‘latest’ version of windows server 2012 there were some updated that probably hadn’t been applied in a timely fashion. Also I was using a non-latest version of the ASP.NET-based blog software that I use. After taking a very selective few backups I turned the machine off for good.
To any sys admins whose systems were attacked by my compromised machine – I’m sorry, I’ll try not to let it happen again. Lesson learned is even a little EC2 micro instance can be useful to attackers. This time around I’m going to try to keep on top of those system updates, and stay up to date with 3rd party software.